
Deploy Sealed Secrets Operator via ArgoCD: A Step-by-Step Guide

Deploying sensitive information securely is a critical task in Kubernetes environment.
Sealed Secrets provides a way to securely manage sensitive data. This guide focuses on how to deploy Sealed Secrets using ArgoCD.
What is Sealed Secrets
Sealed Secrets by Bitnami is a Kubernetes controller and a tool that encrypts your secrets into a SealedSecret resource. This encrypted resource is safe to store in public repositories, as it can only be decrypted by the controller running within your Kubernetes cluster.
How to install Sealed Secrets via ArgoCD
For larger environments, the ArgoCD Vault Plugin or similar is recommended due to the integration capabilities with secrets managers like AWS Secrets Manager or Hashicors vault.
However, Sealed Secrets can be an excellent choice for smaller and simpler setups.
Using Upstream Helm Charts with Custom Values
We'll utilize Bitnami's Sealed Secrets Helm chart while maintaining our custom values file in a private GitHub repository.
Here's a folder structure of the Git repository that I created for this tutorial:
.
├── argocd_applications
│ └── sealed-secrets.yaml
├── charts
│ └── sealed-secrets
│ └── values.yamlWriting the Values File
Instead of writing the values file from scratch, we can leverage the upstream values file provided by Bitnami and customize it according to our needs.
Add the Sealed Secrets Helm repository:
helm repo add bitnami-labs https://bitnami-labs.github.io/sealed-secrets/ Search for available chart versions:
helm search repo bitnami-labs/sealed-secrets --versionsExtract the values file from the latest version (e.g., 2.16.0):
helm show values bitnami-labs/sealed-secrets --version 2.16.0 > charts/sealed-secrets/values.yamlCustomize the values file, for example, by enabling ingress:
ingress:
enabled: true
pathType: ImplementationSpecific
apiVersion: ""
ingressClassName: "nginx"
hostname: "sealed-secrets.devoriales.local"
❗Change the hostname to your hostname
Write the application manifest
In the argocd_applications directory, we define the ArgoCD application manifest for Sealed Secrets. Using a multisource application setup allows us to manage multiple repositories and sources efficiently.
├── argocd_applications
│ └── sealed-secrets.yamlCreate sealed-secrets.yaml with the following content:
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: sealed-secrets
namespace: argocd
spec:
project: default
destination:
server: https://kubernetes.default.svc
namespace: sealed-secrets
sources:
- repoURL: https://bitnami-labs.github.io/sealed-secrets
chart: sealed-secrets
targetRevision: 2.16.0
helm:
valueFiles:
- $values/charts/sealed-secrets/values.yaml
- repoURL: https://github.com/devoriales/manage_devoriales_local_k8s_cluster
targetRevision: main
ref: values
syncPolicy:
syncOptions:
- CreateNamespace=true
automated:
prune: true
selfHeal: true
❗$values resolves to the root of the value-files repository. The $values variable may only be specified at the beginning of the value file path.
Example in my structure:
. ROOT
├── LICENSE
├── README.md
├── argocd_applications
│ └── sealed-secrets.yaml
├── charts
│ └── sealed-secrets
│ └── values.yaml <<<<<< HERE IS THE CUSTOM VALUES FILE
├── sealed-secrets-chart
│ └── sealed-secrets
│ ├── Chart.lock
│ ├── Chart.yaml
│ ├── README.md
│ ├── charts
│ ├── crds
│ ├── templates
│ └── values.yaml
Pushing Files to GitHub
After setting up your repository structure and configuration files, push them to your remote GitHub repository.
git add .
git commit -m "Add Sealed Secrets configuration"
git push origin <your-branch>Applying the ArgoCD Application Manifest
To deploy the Sealed Secrets application, apply the ArgoCD application manifest to your Kubernetes cluster:
kubectl apply -f argocd_applications/sealed-secrets.yaml
Verify the Deployment
In the ArgoCD UI, you can verify the deployment by checking the sync status and health of the Sealed Secrets application:
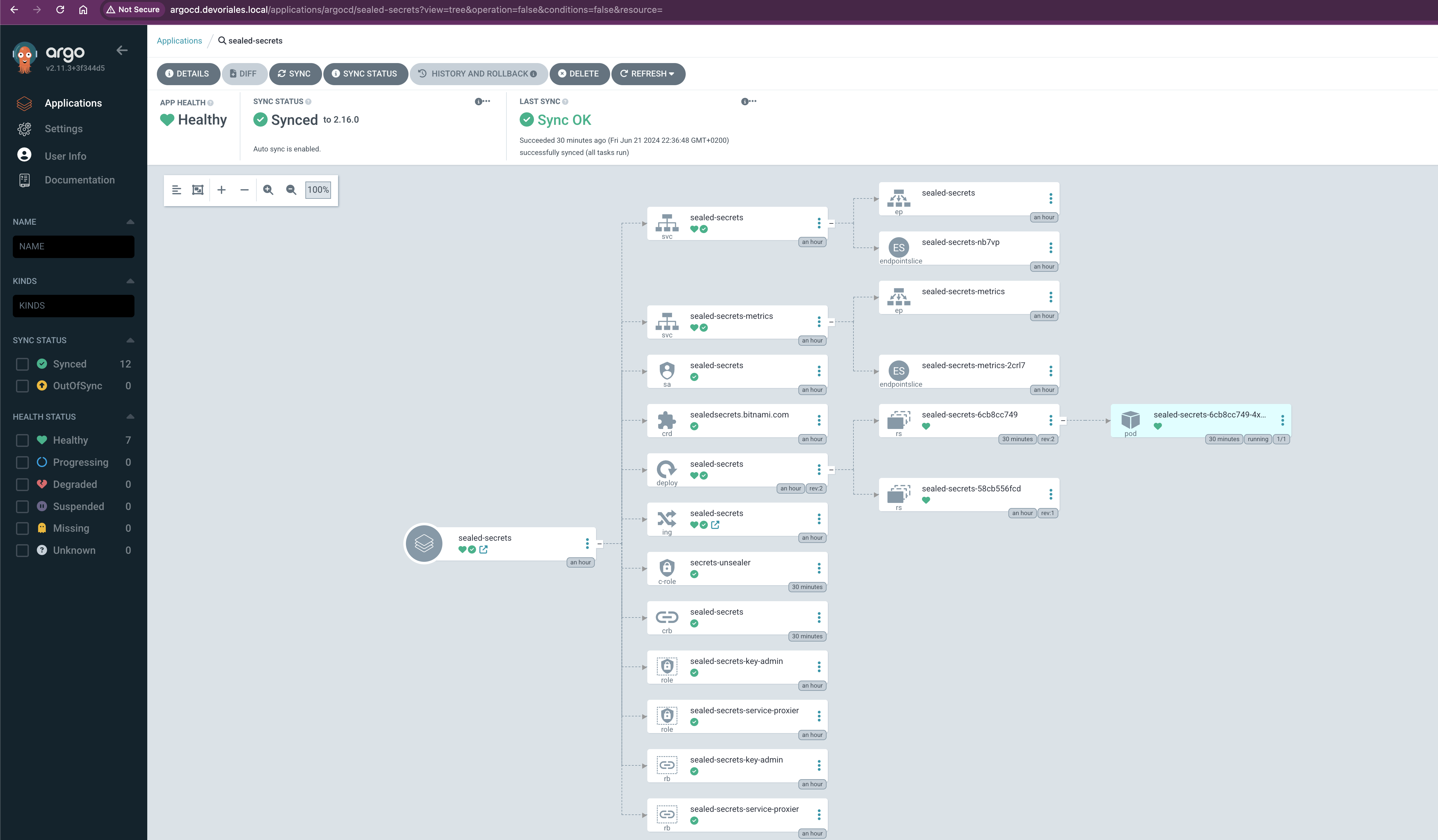
Download the sealed secrets client
To interact with Sealed Secrets, we need to install the kubeseal CLI. Ensure you select the correct version; for Apple Silicon, you need the amd64 architecture.
Download the kubeseal binary:
curl -L -o kubeseal-darwin-amd64.tar.gz https://github.com/bitnami-labs/sealed-secrets/releases/download/v0.27.0/kubeseal-0.27.0-darwin-amd64.tar.gzExtract the package:
tar -xvzf kubeseal-darwin-amd64.tar.gzMove the binary to a directory in your PATH:
mv kubeseal-darwin-amd64/kubeseal /usr/local/bin/kubesealIf the extraction creates a directory, adjust the mv command accordingly.
Verify the kubeseal cli:
kubeseal --help
Output:
Usage of kubeseal:
--add_dir_header If true, adds the file directory to the header of the log messages
--allow-empty-data Allow empty data in the secret object
--alsologtostderr log to standard error as well as files (no effect when -logtostderr=true)
--as string Username to impConclusion
Deploying Sealed Secrets via ArgoCD ensures that your sensitive information remains secure and accessible only within your Kubernetes cluster.
By utilizing a multisource application setup and customizing the Helm chart values, you can maintain a scalable and manageable deployment process.
For larger environments, consider exploring the ArgoCD Vault plugin for more advanced secret management capabilities.