
The runc: CVE-2024-21626 Vulnerability

A vulnerability CVE-2024-21626, has been discovered in runc versions < 1.1.11, the underlying container runtime used by Docker and other platforms. This vulnerability has raised significant alarm due to its potential to allow unauthorized container escape and access to host systems.
ref: https://www.cve.org/CVERecord?id=CVE-2024-21626
runc CRI
Runc is an essential component of container technology. It is a lightweight, portable container runtime that implements the Container Runtime Interface (CRI) for spawning and running containers according to the Open Container Initiative (OCI) specification. Runc is widely used in various container management systems, including Docker, Kubernetes, and CRI-O, making it a foundational piece of the container ecosystem.
Details of CVE-2024-21626
CVE-2024-21626 exposes a critical security flaw in runc that could allow a malicious container to escape its confines and gain unauthorized access to the host machine. This vulnerability stems from improper handling of file descriptors and WORKDIR directive processing. An attacker could exploit this flaw by crafting a container that, when executed, breaks out of its sandbox environment, potentially leading to unauthorized access, data leakage, or even full control over the host system.
Mitigation Strategies
To address CVE-2024-21626, it's crucial to update runc to the latest patched version as soon as possible. Users and administrators should review their container setups and apply updates without delay. In addition to updating runc, it's advisable to:
Regularly scan containers and hosts for vulnerabilities with tools designed for container environments.
Adopt container security best practices, including least privilege user controls, secure container configurations, and network segmentation.
Monitor container activity and host access patterns for unusual or unauthorized behavior.
Check Vulnerabilities Frequently
We should always fight the evil and keep vulnerabitilies away from our clusters.
To do that we need to be equipped with some good weaponary.
I have some favorite security tools I'd like to mention, each offering unique features that cater to different aspects of security vulnerability management.
Starboard from Aqua Security
This tool is my absolute favourite.
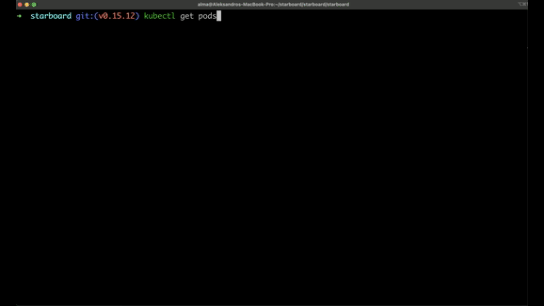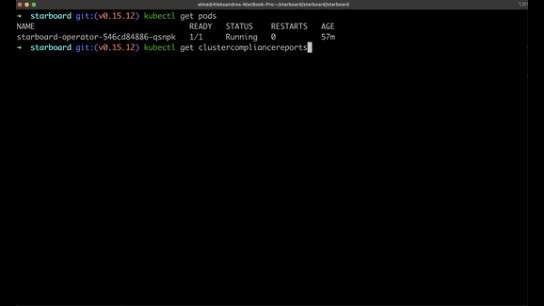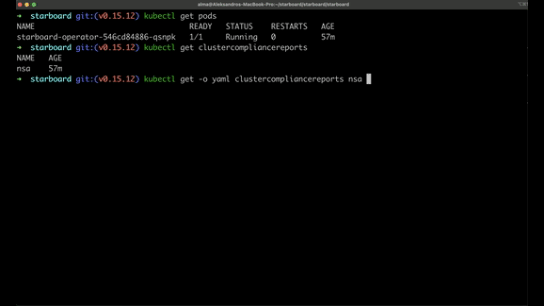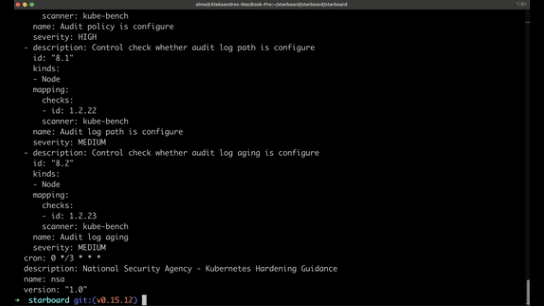
Starboard integrates into the Kubernetes environment and runs as an operator.
It provides detailed vulnerability reports for containers and Kubernetes configurations, making it easier to identify and address potential security issues.
Please note, Starboard uses Trivy scanner to scan the images .
What I also like is, you can configure Starboard to scan GitHub repos and wide
https://aquasecurity.github.io/starboard/v0.15.1/
Trivy Scanner
Trivy is capable of scanning containers, serverless, and IaC (Infrastructure as Code) for vulnerabilities, ensuring a broad security coverage.
It offers a straightforward CLI interface that produces detailed scan results, highlighting vulnerabilities across OS packages and application dependencies.
I usually recommend trivy scanner to be used as part of CI pipelines since it can be nicely integrated into i.e. GitHub Workflows and pick up the vulnerabilities before it gets deployed to the cluster.
Kubescape
Another really good tool that checks the compliancy against several security frameworks including NSA-CISA, MITRE ATT&CK and the CIS Benchmark.
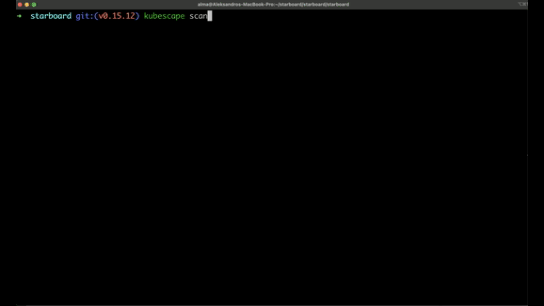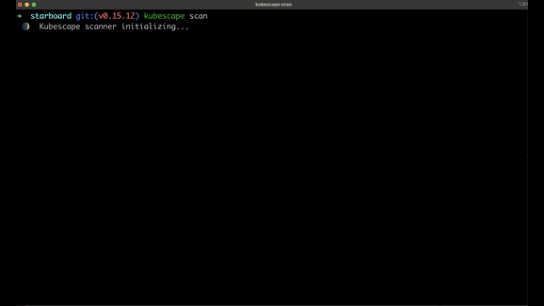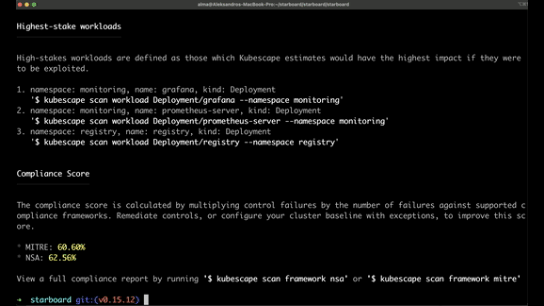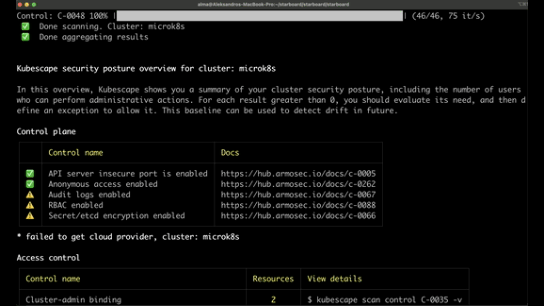
It offers guidance on fixing identified issues, prioritizing them based on their impact which really nice.
Armo, the company behind this open-source project, offers additional paid services, including their Dashboard, where you can perform deeper analysis.
Conclusion
As we've walked through the discovery of CVE-2024-21626 within runc versions prior to 1.1.11 serves as a strong reminder to keep your cluster up-to-date.
The critical nature of CVE-2024-21626 with its potential for unauthorized container escape and host system access, cannot be overstated. It highlights the essential role of container runtimes like runc in maintaining the integrity of containerized environments across numerous platforms, including Docker, Kubernetes, and CRI-O. A
In our discussion, we also walked though some of the tools that can help —Starboard, Trivy Scanner, and Kubescape—each offering own capabilities to detect, analyze, and mitigate vulnerabilities.