LATEST
Master DevOps: Docker, Kubernetes, CI/CD, and other cloud technologies
Discover the essentials of DevOps technologies with our focused tutorials. Master tools like Docker, Kubernetes, CI/CD pipelines, and cloud services. Our practical, hands-on approach will unlock your potential in tech innovation.
Learn new concepts with our Video Shorts
Today's Slide
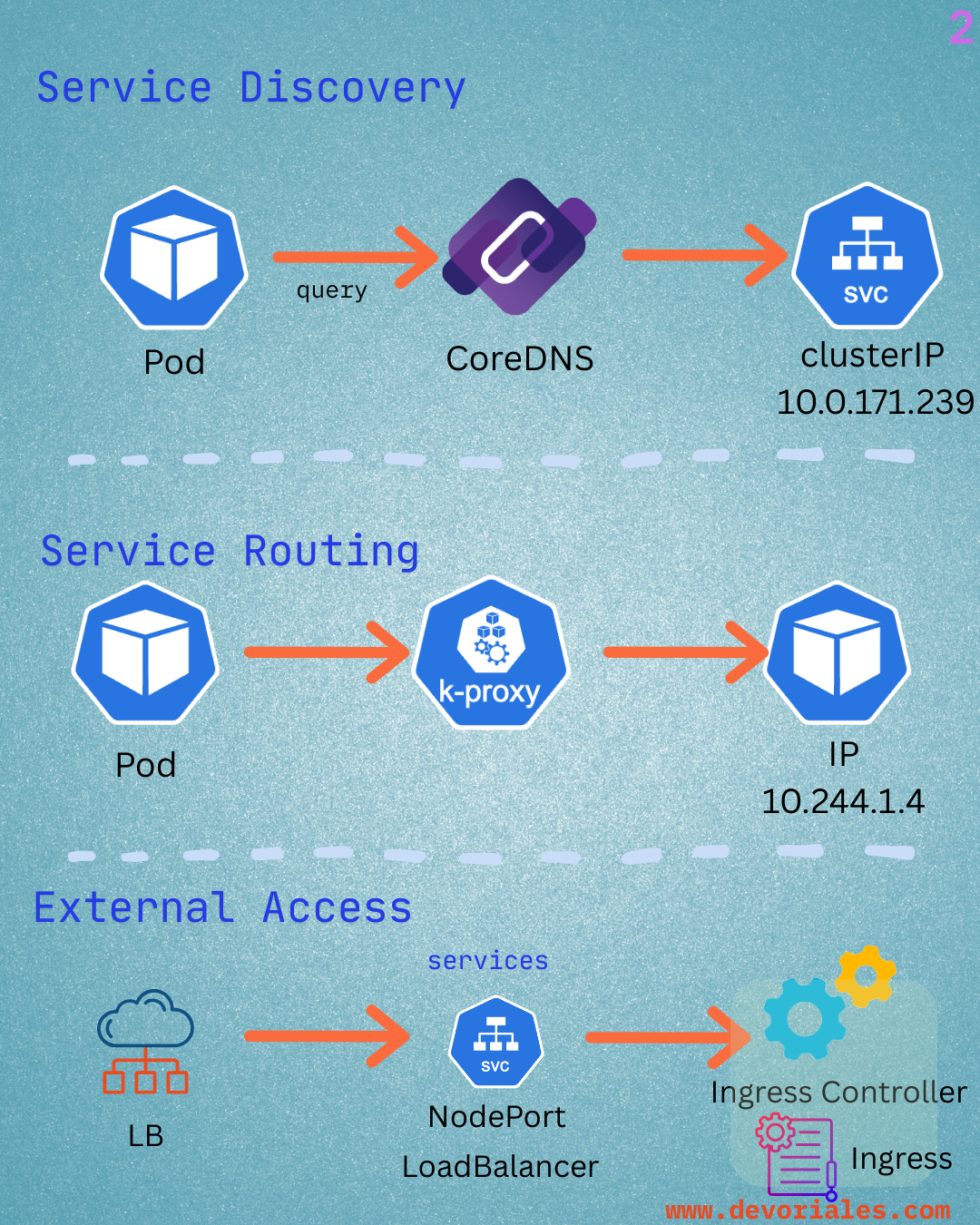
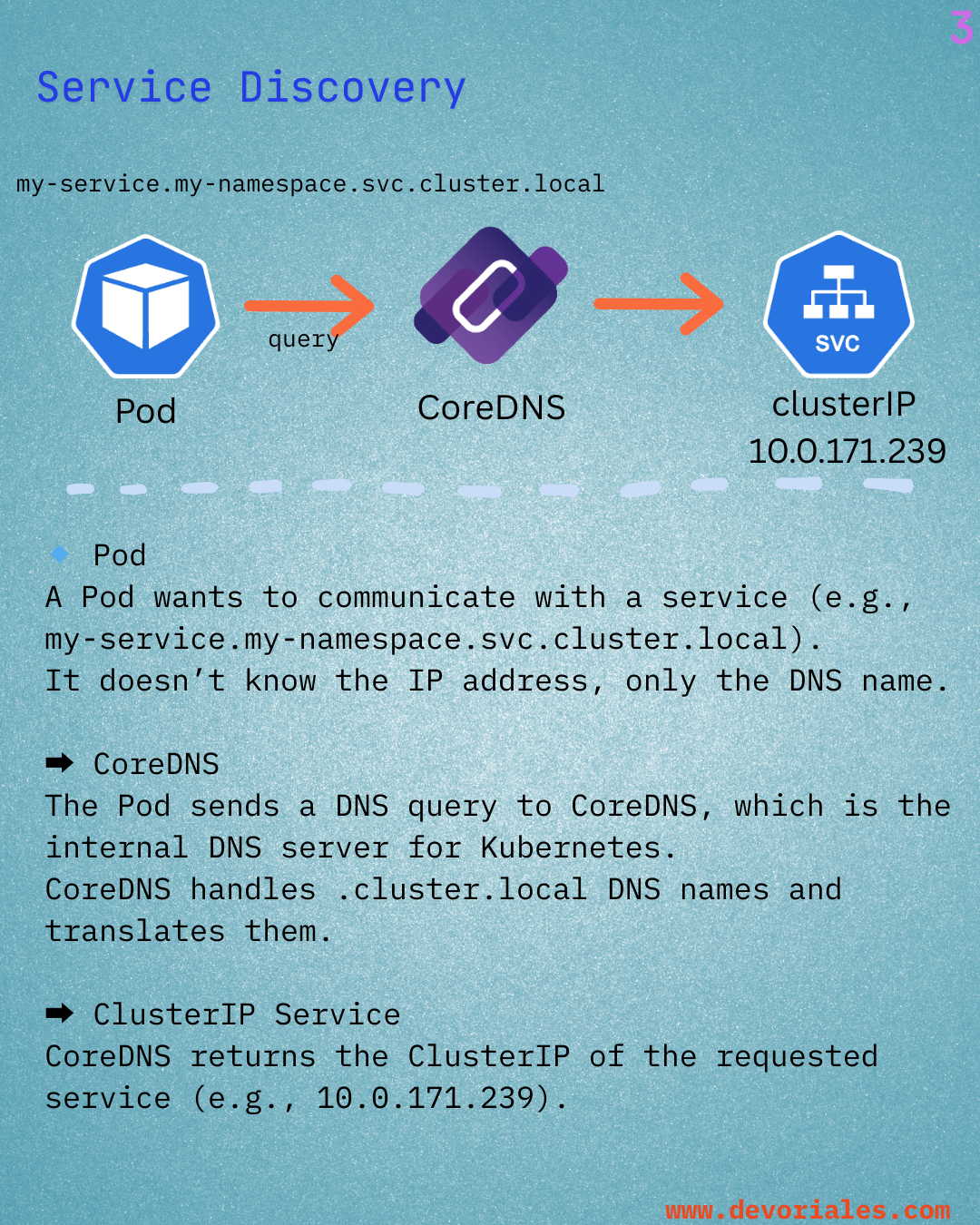
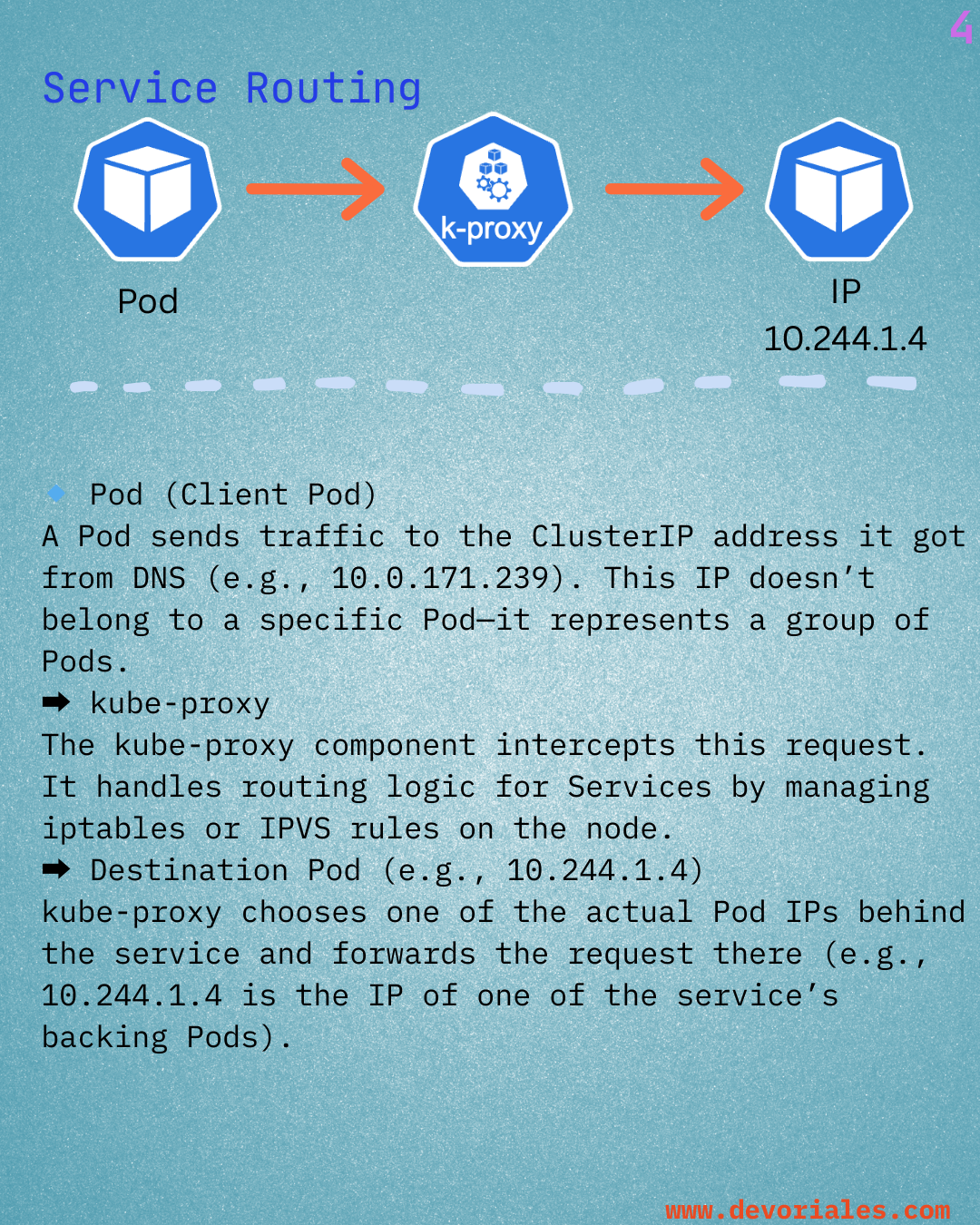
View More SlidesLearn: Learn Kubernetes Networking
Latest Blog Posts
View More Posts





What to Consider If You're Not Signing Up for Bitnami Premium
news TechNews helmPosted on 2025-02-12



Python Tops the Tiobe Index: The Most Popular Programming Languages - January 2025
dev coding newsPosted on 2025-01-07